What is proxy communication?
Is it correct to understand the working level of forward proxy reverse proxy transparent proxy?
Forward proxy and reverse proxy (application load balancing, some NG reverse proxy) can be understood as a man-in-the-middle mode. At the same time, both ends establish a TCP connection, and then the man-in-the-middle performs TCP connection between the two ends.
Can a transparent proxy be understood as a simple and crude "hijacking" of a passing data packet, without splitting the complete TCP connection into two independent segments. So, in this sense, this kind of transparent proxy is similar to the working hierarchy of NAT devices?
Preface
I once saw a person write tens of thousands of words to answer a question, and read it after three days. Shocked, what is all this for? These words can produce a book, and it is also a reward for your hard work. However, I think the man has always been happy, but there is no doubt that his reputation (Reputation) is in full swing. When technical workers have accumulated to a certain degree, they need to use some text to record these knowledge points, and a good problem is a good writing opportunity. This is also my idea. I want to use text to record the knowledge points of the computer network. For later learners reference. Because computer networks are all-encompassing, it is impossible to write according to chapters. It is a boring and tedious process, so I collected almost all the questions about computer networks and answered them according to priority. When all these questions are answered, all chapters of the computer network will be completed, which is equivalent to giving away to friends who have been paying attention to the public account for free.
If your friends have a little foundation, it may be more rewarding to read. The public account has a readership of nearly 20,000 people, and the technical level of the readers is divided into several levels. It is impossible for all articles to start from 0. Knowledge points are somewhat fragmented, and long-term reading will make them organically integrated to form a systematic knowledge framework. With a solid computer network foundation, no matter what you study, you will be familiar with it. Okay, let's officially enter today's topic. . .
text
Client / server communication model When you first learn computer network communication, you must have learned the client / server communication mode. That is, the server starts first, listens to a port, and quietly waits for clients from all over the world to contact the port and establish a connection with the port, and then data can flow bidirectionally on the connection.
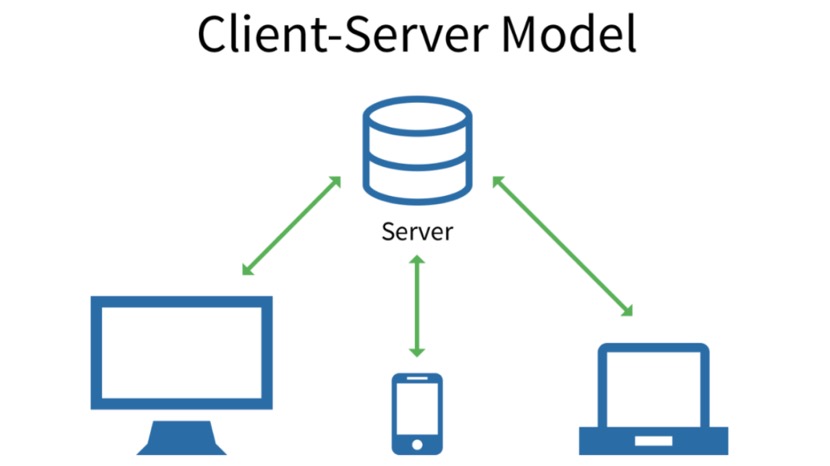
Under this model, the client sees that the server's IP is the real server IP, and the server sees that the client's IP is the real client IP. But this model is just an ideal model, and such an ideal model can hardly be found in today's Internet communication. All this is caused by the shortage of IPv4 addresses.
Transparent agent communication model
Due to the shortage of public IPv4 addresses, all computers, mobile phones, and iPADs in a home LAN cannot be configured with public IPv4 addresses, but can only use private IPv4 addresses. Private IPv4 addresses are as follows:
10.x.x.x
172.16.x.x – 172.31.x.x
192.168.x.x
When they communicate with servers on the Internet, before their IP packets leave the home router, the router needs to replace their IPv4 address (private) with a public IPv4 address. Who is this public IPv4? Of course, it is the external network interface of the router, more precisely, the operator temporarily leases it to the external network interface of the router (distributed through PPPoE protocol).
Obviously, when this IP packet reaches the server, the server sees that the client's IPv4 address is the router's public IP, not the client's real IPv4 address (private). This communication model is no longer a client / server communication model in a strict sense. For the sake of distinction, it can be called transparent proxy communication.

The air, which is invisible but exists, is transparent. The user cannot see the existence of the agent, but it actually exists. This is the origin of the transparent agent communication.
The reason for choosing to be transparent to users is to simplify the configuration of users! Imagine that if you don't use a transparent proxy, but manually configure the proxy, every computer, mobile phone, iPAD that needs to be connected to the Internet needs to be set up. What a huge workload this is worldwide!
With the transparent proxy, users can communicate with the server on the Internet by plugging in the Internet line or connecting to the wireless. The transparent proxy is quietly completed by the router.
Does the transparent proxy (router) change the private source IP + port number to the public network IP + port number and save it in the NAT table? Or does the transparent proxy establish a TCP connection with the client, the transparent proxy establishes another connection with the server, and then pinches the two connections together to seamlessly connect the two connections?
Generally speaking, home wireless routers and enterprise office routers use the former, while some high-end firewalls use the latter, that is, two connections. The advantage of this is that since the firewall has the full TCP connection status, it can better control the TCP connection.
There is a more important reason. Today's Internet communications are mostly transmitted in encrypted form (https). If the firewall does not decrypt the https message, the https communication will be a blind spot for supervision. The ghosts and snakes are mixed in https, illegal files are embedded in encrypted mail, and the firewall is powerless to them. Obviously this is unreasonable!
Therefore, when the firewall communicates the TCP connection through https, it starts the transparent proxy work and completes the TCP connection. Immediately after entering the SSL / TLS handshake phase, the self-signed certificate of the firewall is used to deceive the client, so that the firewall establishes a TLS secure connection with the client.
Firewall and client
TCP connection + TLS secure connection
Firewall and server
TCP connection + TLS secure connection
In this way, the firewall can decrypt the encrypted messages from the client, and also decrypt the encrypted messages from the server. The firewall can do the work of reviewing, logging and filtering.
Readers may say, but I grabbed packets on the client, and I clearly saw the server's public IP, but I didn't see the firewall's IP!
This is very easy to understand. The secret of the firewall is "spoofing". When the client's message to the server reaches the firewall, the firewall immediately begins to impersonate the server to communicate with the client. Of course, the server's IP is used.
The above is the news sharing from the PASSHOT. I hope it can be inspired you. If you think today' s content is not too bad, you are welcome to share it with other friends. There are more latest Linux dumps, CCNA 200-301 dumps and CCNP Written dumps waiting for you.
Comments
Post a Comment